Smart Card Manager application¶
- This application is made available to users to perform basic card management functions on cards or cryptographic USB keys. In addition, it provides a quick and convenient way to:
Obtain information about the card or USB key, including its identification and capabilities
Access information stored on the token, such as keys and certificates
Allow content management, such as password profiles, or password modifications
Import certificates and digital keys between a computer and a card.
Smart card management is accessed via the following icon in the toolbar :

Smart cards and keys¶
This section lists the card readers, the cards or cryptographic USB keys inserted, and the certificates present on the cards.
Reader and card icons¶
|
Smart card reader without connected card. |
|
Smart card reader with a supported card connected. |
|
Cryptographic USB key. |
|
Smart card reader with an unsupported card connected, or reading failed (mute card). |
|
Virtual reader containing an card unknown from middleware detected. |
Page content¶
If the selected drive/card pair contains certificates, they are displayed in the tree in the left-hand pane, below the reader:
User certificates
Certification authority (CA) certificates
When a reader/card pair is selected in the tree, the information below is displayed in the right-hand pane:
General information
PINs
Objects
The General information section provides information on the card and reader, such as manufacturer, serial number and card profile.
The PINs section¶
The PIN section is only displayed when a smart card or key is selected. It is used to unlock the object. Two types of PIN may be present on the card:
Card PIN (or global PIN)
Signature PIN (reserved for qualified signature operations), for the cards concerned.
PINs are displayed with the following icons:
|
PIN not verified, with test counter at maximum. |
|
PIN verified (private objects accessible). |
|
PIN whose test counter is not at maximum. |
|
PIN whose trial counter is blocked. |
Four operations are possible on PINs:
Verify: enables access to associated private objects (notably private keys). To do this, you will be asked to enter your PIN. Please note: the number of attempts is generally limited. Removing the card does not reset the counter. Entering the correct code resets the counter.
Logout: cancels PIN verification, and therefore remove access to associated private objects.
Change: allows you to change the PIN. The current PIN will be requested. Please note: the number of attempts is generally limited (same counter as above). In addition, various constraints may apply to the choice of the new PIN code.
Unblock: for cards supporting this operation. Allows you to reset a confidential code when the number of attempts has been exhausted. To do this, you will be asked to enter an unlock code. Please note: the number of times you can use this code may be limited. A new confidential code must then be defined.
The Objects section¶
This section presents the certificates and keys contained in the card. Please note that private objects are only visible if the associated PIN has been verified beforehand.
Objects are presented with the following icons:
|
Certificate |
|
Key |
Trust verification of certificate¶
For information purposes, trust verification of certificate is represented by the following icons:
|
Valid certificate |
|
Invalid certificate (expired, not approved, revoked, …) |
|
Certificate which validity could not be verified (no TSL case) |
|
Certificate which validity could not be verified (TSL case) |
Note
Both TSL and no TSL cases are defined by the state of Certificate verification policy (cf. User options).
Several rules are taken in account to determine check trust of a certificate:
A certificate — if it’s not a root certificate — without the associated private key in the card is always seen as invalid.
A certificate is invalid if it’s correctly verified (date, signature…) and its whole trust certificate chain is also verified. Certificates taken in account for the trust chain can be present in system certificate store, or in online Trusted Services List (TSL) or in the card; depending on the Certificate verification policy (cf. User options) setting.
Case where validity could not be verified because trust chain could not be verified. There are two cases, depending on the state of Certificate verification policy :
no TSL case: if the trust chain is incomplete and the certificate has a valid date.
TSL case: if verification could not be done because the online Trusted Services List (TSL) is not reachable (no network connection…).
A certificate is invalid otherwise.
Objects section operations¶
The section can be structured in different ways:
|
Displays all objects, sorted by container (linked objects are grouped together) |
|
Only displays certificates |
|
Displays all object |
The associated menu allows you to :
import a certificate, key pair or complete container from a PKCS#8, PKCS#12 or X.509 format file.
generate an RSA or elliptic key pair (for cards supporting it).
These operations may not be available depending on the middleware version deployed, or the operations supported by the card profile.
When hovering over a certificate or key, a + button allows to display detailed information.
The contextual menu on an object allows to :
export the certificate (in DER or PEM format), or the public key (as a CSR)
delete the object
Possible card operations¶
Note
Not all operations are available on all middleware versions and for all cards.
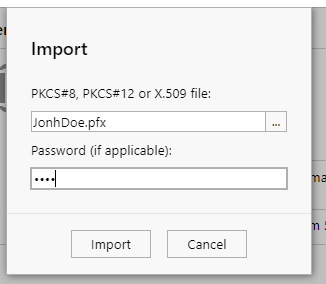
Import a certificate¶
This operation allows you to import a PKCS#8, PKCS#12 or X.509 certificate into the card. To do this, you need to enter the card PIN and any certificate password.
Generate a key pair¶
This operation generates an RSA or elliptic key pair directly on the card.
This operation may take some time.
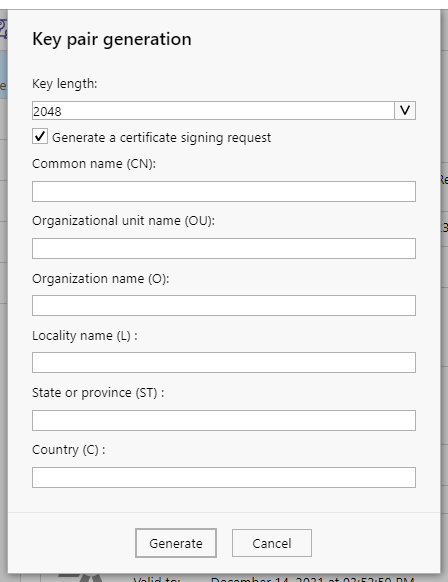
Once the operation is complete, a new key pair is visible on the manager interface.
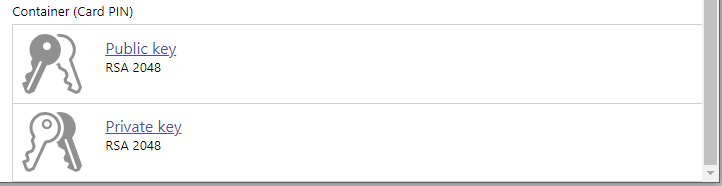
Export a certificate¶
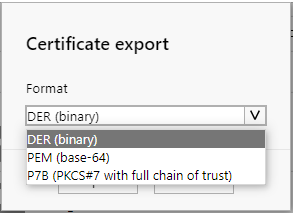
This operation exports a certificate in DER, PEM or PKCS#7 format to the user workstation.
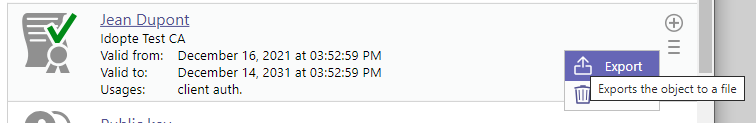
You can select the format before exporting:
Delete an object¶
You can delete an object (key or certificate) from the menu :
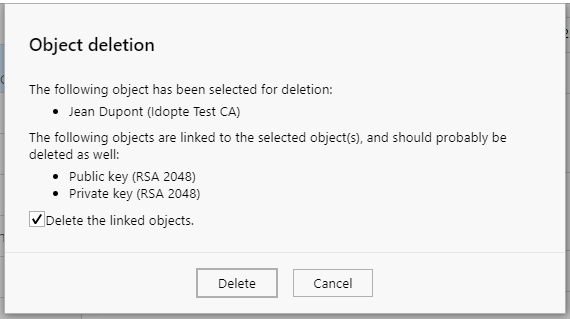
By default, linked objects are also deleted:
Certificate stores¶
This section lists the certificates stored in the Microsoft Windows store. These can also be accessed via the certmgr.msc command.
This section may not be available depending on the version of middleware installed.